At this yr’s annual hacking convention, Black Hat Asia, a group of safety researchers revealed how cybercriminals are sneakily utilizing stolen bank cards and Apple Retailer On-line’s ‘Another person will decide it up’ choice in a scheme that has stolen over $400,000 in simply two years.
9to5Mac Safety Chew is completely delivered to you by Mosyle, the one Apple Unified Platform. Making Apple gadgets work-ready and enterprise-safe is all we do. Our distinctive built-in method to administration and safety combines state-of-the-art Apple-specific safety options for absolutely automated Hardening & Compliance, Subsequent Era EDR, AI-powered Zero Belief, and unique Privilege Administration with probably the most highly effective and fashionable Apple MDM available on the market. The result’s a very automated Apple Unified Platform at present trusted by over 45,000 organizations to make hundreds of thousands of Apple gadgets work-ready with no effort and at an inexpensive value. Request your EXTENDED TRIAL right now and perceive why Mosyle is every thing you want to work with Apple.

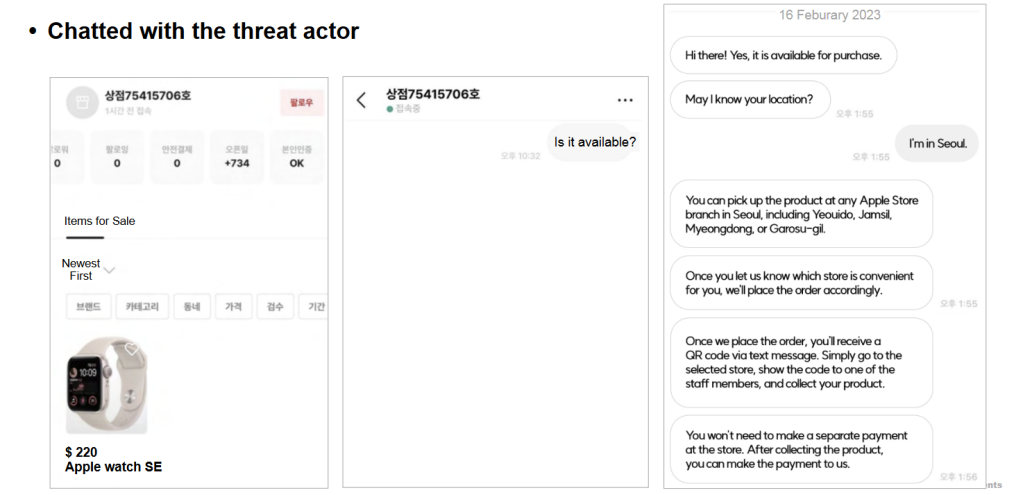
In keeping with Gyuyeon Kim and Hyunho Cho with the Monetary Safety Institute of South Korea, in September 2022, she and her colleague uncovered a string of cyberattacks in opposition to greater than 50 reliable on-line shops, exposing main knowledge breaches that had occurred. Nonetheless, upon additional evaluation, they discovered risk actors have been excited about greater than a fast heist of person knowledge.
The cybercriminals managed to govern the fee pages of those on-line shops to transmit bank card and private data to their servers, along with the reliable ones, to assist stay undetected.
“These risk teams employed numerous evasion methods to forestall detection of their phishing pages by website directors and customers, utilizing a number of vulnerabilities and instruments,” the safety duo acknowledged of their Black Hat briefing.
Nonetheless, stealing bank cards was only one a part of the plan.
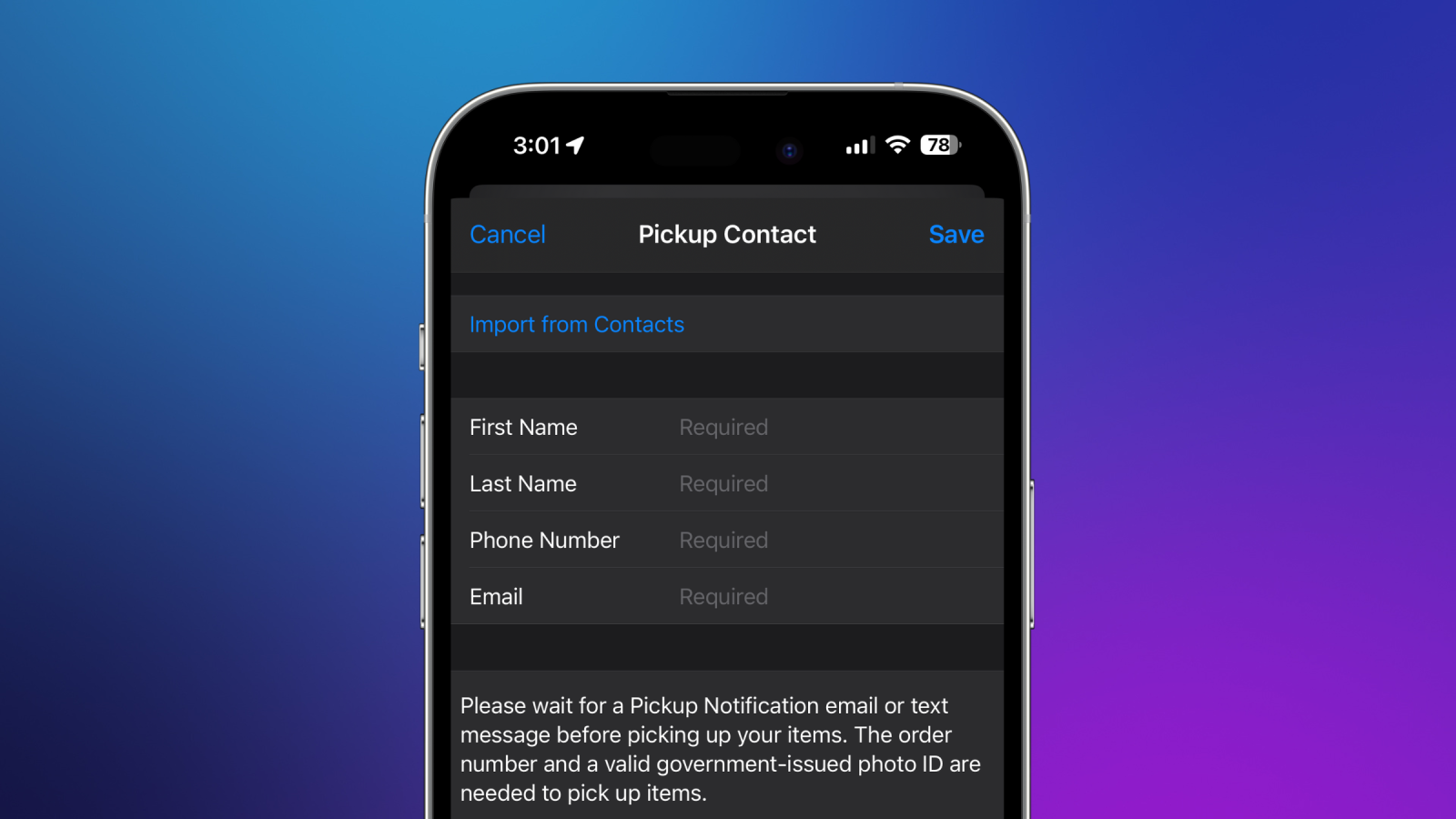
One of many risk actor’s major methods of cashing in was leveraging Apple Retailer On-line’s ‘Pickup Contact’ coverage, based on the research. “The last word goal of this operation was monetary achieve,” defined Kim.
The scheme begins with promoting new Apple merchandise at “discounted” costs in second-hand on-line shops in South Korea. From what the analysis describes, these seem like the equal of a Craiglist or eBay. When the customer reaches an settlement with the vendor, or on this case, the risk actors, beforehand stolen card credit score particulars are used to buy the precise product from the Apple Retailer.
Picture by way of Black Hat Asia/Gyuyeon Kim and Hyunho Cho
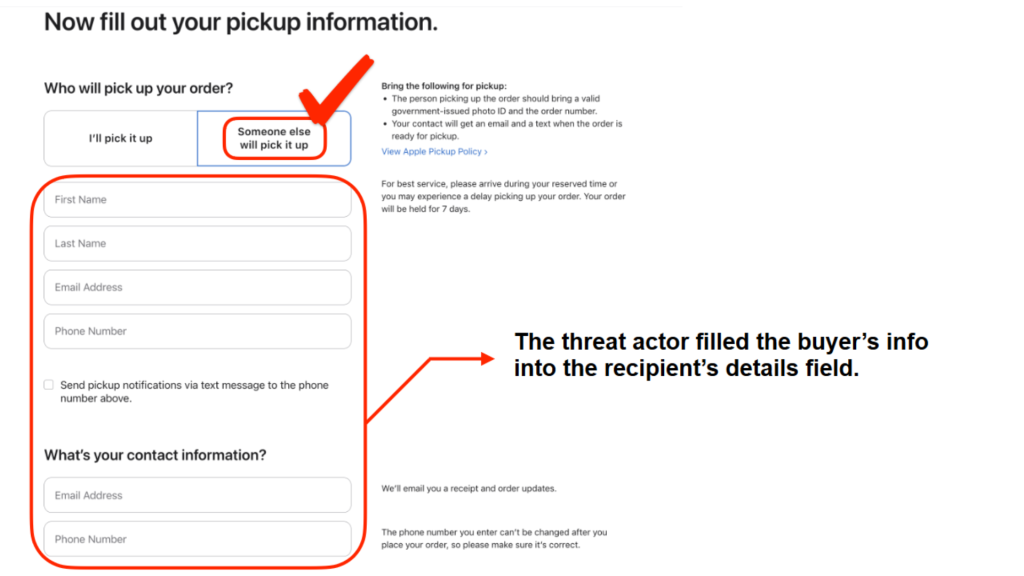
As an alternative of getting it shipped, the cybercriminals set the merchandise to the ‘Another person will decide it up’ choice on Apple’s web site. This enables licensed people to select up on-line orders at an Apple retail retailer by presenting a authorities photograph ID and QR code/order quantity. The client from the second-hand retailer can be designated because the third occasion in a position to decide up the product that was unknowingly bought with a stolen bank card.
Solely after the customer picks up the product do they pay, presumably by the second-hand retailer. The risk actor might miss out if the customer doesn’t ship the agreed-upon quantity.
As an example, a brand-new iPhone 15 value $800 might be listed for $700 on the second-hand market. The worth can be low sufficient to draw curiosity however excessive sufficient to not seem as a rip-off. After discovering an purchaser, the criminals would buy the system utilizing a stolen bank card quantity obtained by their phishing operations and pocket the $700 paid by the customer from the second-hand retailer.
Picture by way of Black Hat Asia/Gyuyeon Kim and Hyunho Cho
“A stolen card was used to make a $10,000 fee at an Apple retailer, however Apple’s refusal to cooperate as a consequence of inside rules has hindered the investigation,” citing the researcher’s presentation at Black Hat Asia in a extra excessive case. “Regardless of Mr. Yoon’s efforts to report the incident to each the cardboard firm and the police instantly, Apple’s lack of cooperation has led to over a month of investigation delays. Apple’s refusal to offer any data, citing inside coverage, has sparked criticism each domestically and in the US, regardless of the corporate’s emphasis on privateness safety.”
Gyuyeon Kim and Hyunho Cho name the scheme “PoisonedApple,” which they consider has generated $400,000 over the previous two years. The present scope is South Korea and Japan, however there’s no motive criminals in different nations, together with the US, might start doing the identical.
Who’s behind the scheme?
The researchers consider the culprits are primarily based someplace in China as a result of phishing internet pages being registered by a Chinese language ISP. Miraculously, whereas combing by darkish internet boards, in addition they discovered mentions in simplified Chinese language of the identical electronic mail deal with within the supply code.
Take a look at the total Black Hat briefing and presentation right here.
Extra on this collection
Comply with Arin: Twitter/X, LinkedIn, Threads
FTC: We use revenue incomes auto affiliate hyperlinks. Extra.


