
Edgar Cervantes / Android Authority
TL;DR
- Android 15 may introduce a brand new Enhanced Affirmation Mode that makes it more durable for malicious apps to take advantage of an OS loophole.
- Android blocks customers from simply enabling the Accessibility or Notification Listener providers of apps which might be sideloaded from exterior an app retailer.
- Nevertheless, the tactic that Android makes use of for this has a loophole in it that Android 15 will shut.
Though most Android customers obtain apps from preloaded app shops like Google Play, some customers get their apps from various on-line sources, a observe known as sideloading. That is potential as a result of Android lets customers set up third-party apps with out the Google Play Retailer as long as they get their palms on the mandatory app set up information. The flexibility to freely sideload apps is an enormous a part of what makes Android a extra open platform than iOS. Sadly, it’s additionally the explanation why individuals erroneously imagine that Android is much less safe than iOS.
That’s as a result of no matter the place you supply apps from, Android’s built-in privateness and security measures guarantee they will’t entry delicate permissions with out your consent. Nevertheless, it’s true that sideloading apps from various on-line sources carries a bit extra danger for the common person when in comparison with sticking with Google Play. It’s because it’s merely simpler for malicious builders to distribute apps exterior of Google Play since they don’t must cope with the rules, forms, and scrutiny that Google Play app distribution entails.
Malicious Android apps, regardless of the place they’re sourced from, generally attempt to trick customers into granting them entry to the Accessibility and Notification Listener APIs due to their energy. The Accessibility API lets apps learn the content material of the display and likewise carry out inputs on behalf of the person, whereas the Notification Listener API lets apps learn or take motion on any notification. These APIs can be utilized to commit advert fraud, steal one-time passwords (OTPs), set up further payloads, and do a lot, rather more.
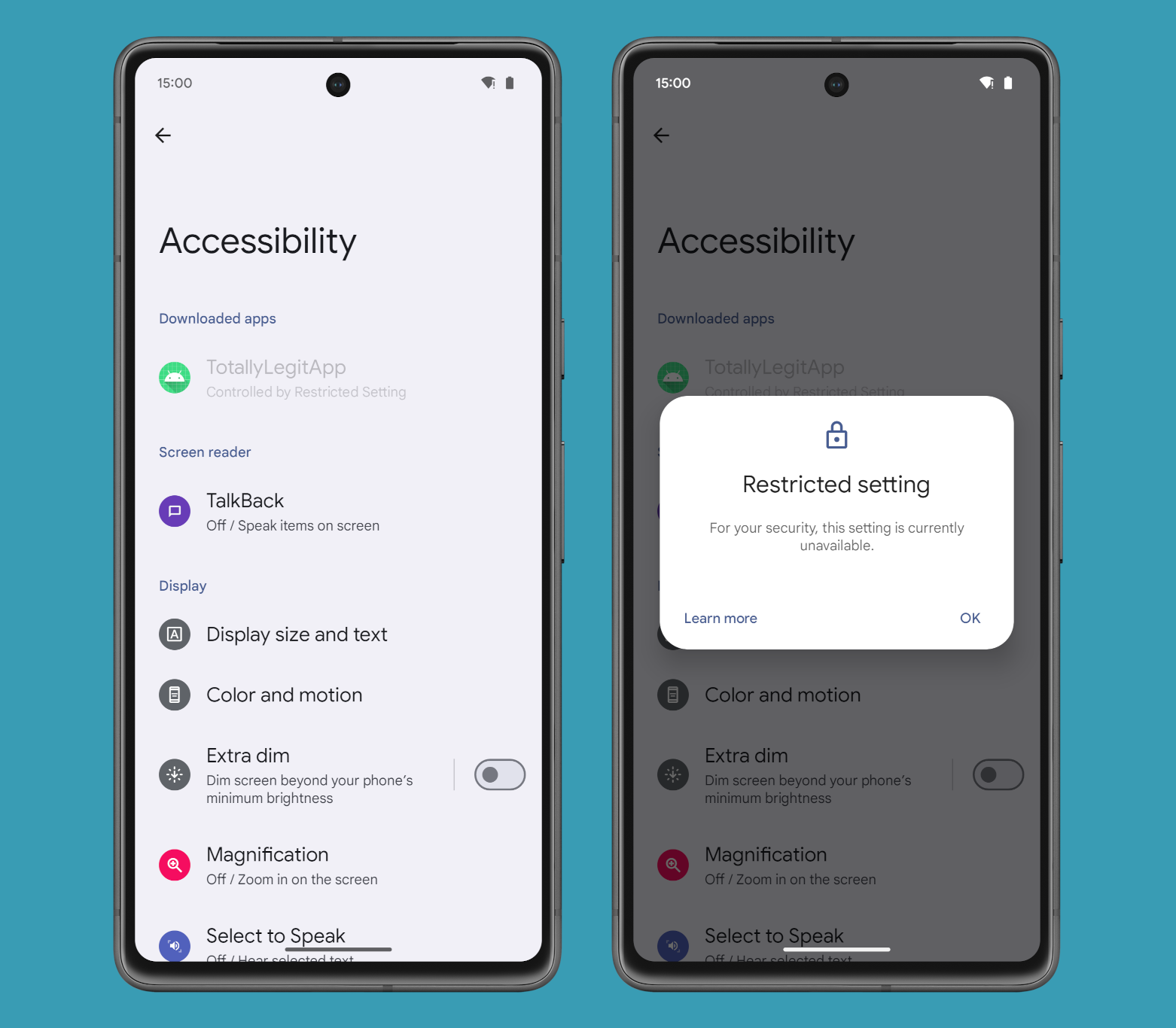
Whereas Google Play has some (largely bureaucratic) measures to make sure these APIs are used for his or her meant functions, Android itself depends totally on the app’s personal declarations to determine how a lot entry to grant. For instance, beginning in Android 13, the working system prevents customers from simply enabling the Accessibility or Notification Listener providers of apps that have been sideloaded from exterior of an app retailer. For those who have been to, say, sideload an app despatched to you by way of e mail, then Android would block you from enabling that app’s Accessibility or Notification Listener service as they’re marked as “restricted settings.”
Mishaal Rahman / Android Authority
How does the OS know when apps are sideloaded from exterior of an app retailer? It determines this primarily based on whether or not or not the app that did the set up used Android’s session-based set up APIs (that are generally however not solely utilized by app shops) versus Android’s non-session-based set up APIs (that are generally utilized by file managers, internet browsers, and different apps with generic file downloading assist). The issue with this strategy is that any app can make the most of Android’s session-based set up APIs to sideload one other app, that means there’s no assure {that a} reliable, third-party app retailer is definitely the one which’s doing the sideloading. Malicious app builders have sadly acknowledged this loophole in Android’s Restricted Settings function and have already been exploiting it to bypass this safety function.
Luckily, Google is engaged on closing this apparent loophole in Android’s Restricted Settings function. In Android 15, the corporate is getting ready to introduce a brand new “Enhanced Affirmation Mode” function that’s mainly a tighter, extra souped-up model of Restricted Settings. Though the Enhanced Affirmation Mode function isn’t but enabled within the newest Android 15 Beta 1.1 replace, I analyzed the code and defined the way it’ll work in some element.
For starters, the wording within the Enhanced Affirmation Mode dialog carefully matches the prevailing Restricted Settings dialog. Similar to with Restricted Settings, the ECM dialog will say, “to your safety, this setting is presently unavailable” if you attempt to allow an app’s Accessibility or Notification Listener service. Nevertheless, the dialog will broaden on the reasoning a bit by including that “this app has requested the %1$s permission, which is a restricted setting as a result of it may possibly put your safety & privateness in danger. Restriction to this permission could forestall this app from working.” Aside from that, the remainder of the dialog is identical, all the way down to the title and the 2 buttons.
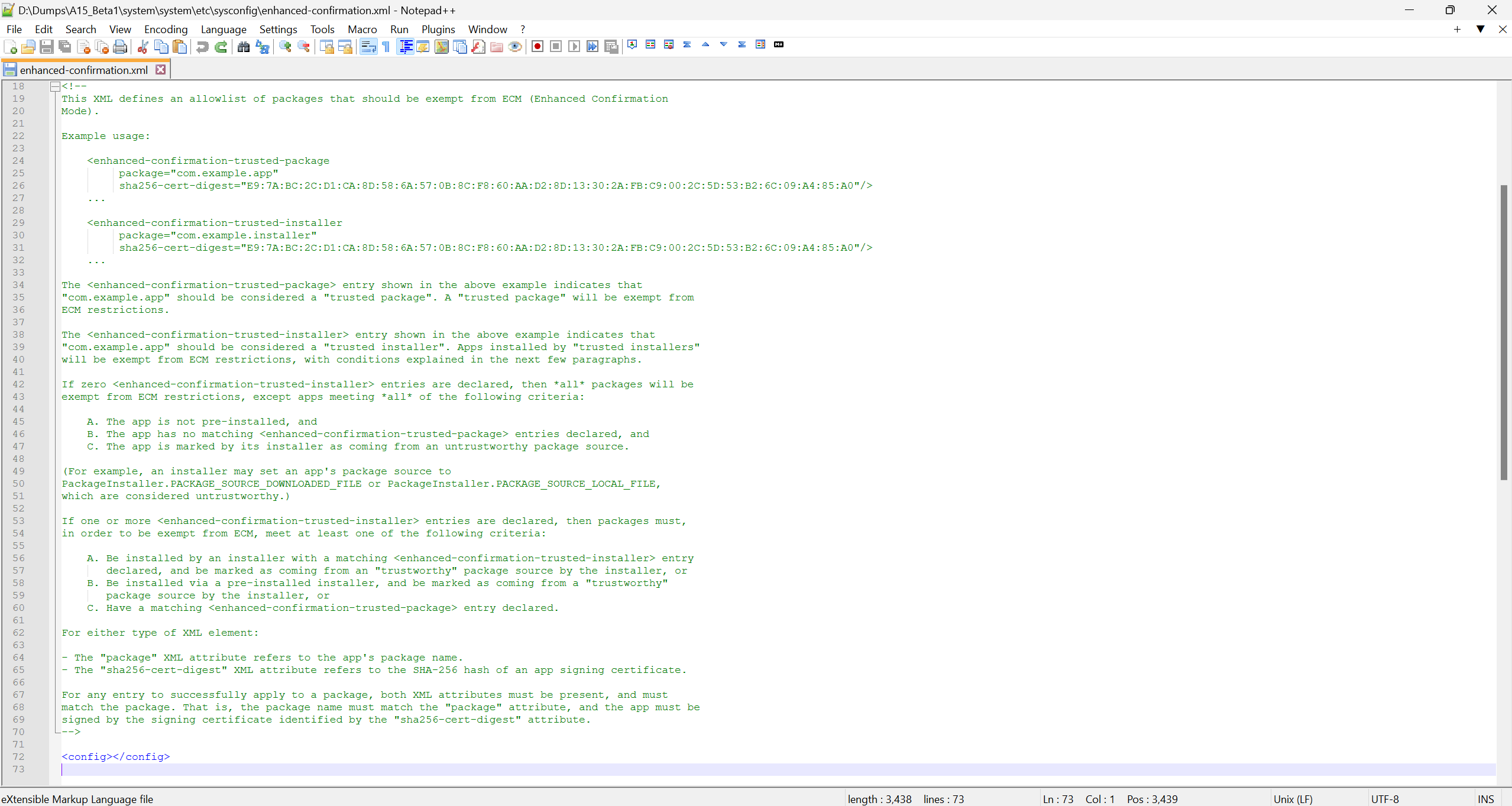
One essential distinction between Android 15’s new Enhanced Affirmation Mode and Android 13’s Restricted Settings function is how they’re enforced. As an alternative of differentiating primarily based on what set up APIs have been used, Enhanced Affirmation Mode in Android 15 checks an allowlist that’s preloaded within the manufacturing facility picture. This allowlist is an XML file situated within the /system/and so on/sysconfig path of Android 15, and it determines which packages and installers are exempt from any restrictions.
Mishaal Rahman / Android Authority
Any packages which might be explicitly allowlisted within the XML file are thought-about “trusted packages” and are exempt from ECM restrictions. Equally, any installers which might be listed within the XML file are thought-about “trusted installers,” which implies the apps they then set up are eligible to be exempt from ECM restrictions. An app put in by a “trusted installer” is exempt from ECM restrictions if it’s marked as coming from a “reliable” bundle supply (i.e., it’s not marked as PACKAGE_SOURCE_DOWNLOADED_FILE or PACKAGE_SOURCE_LOCAL_FILE).
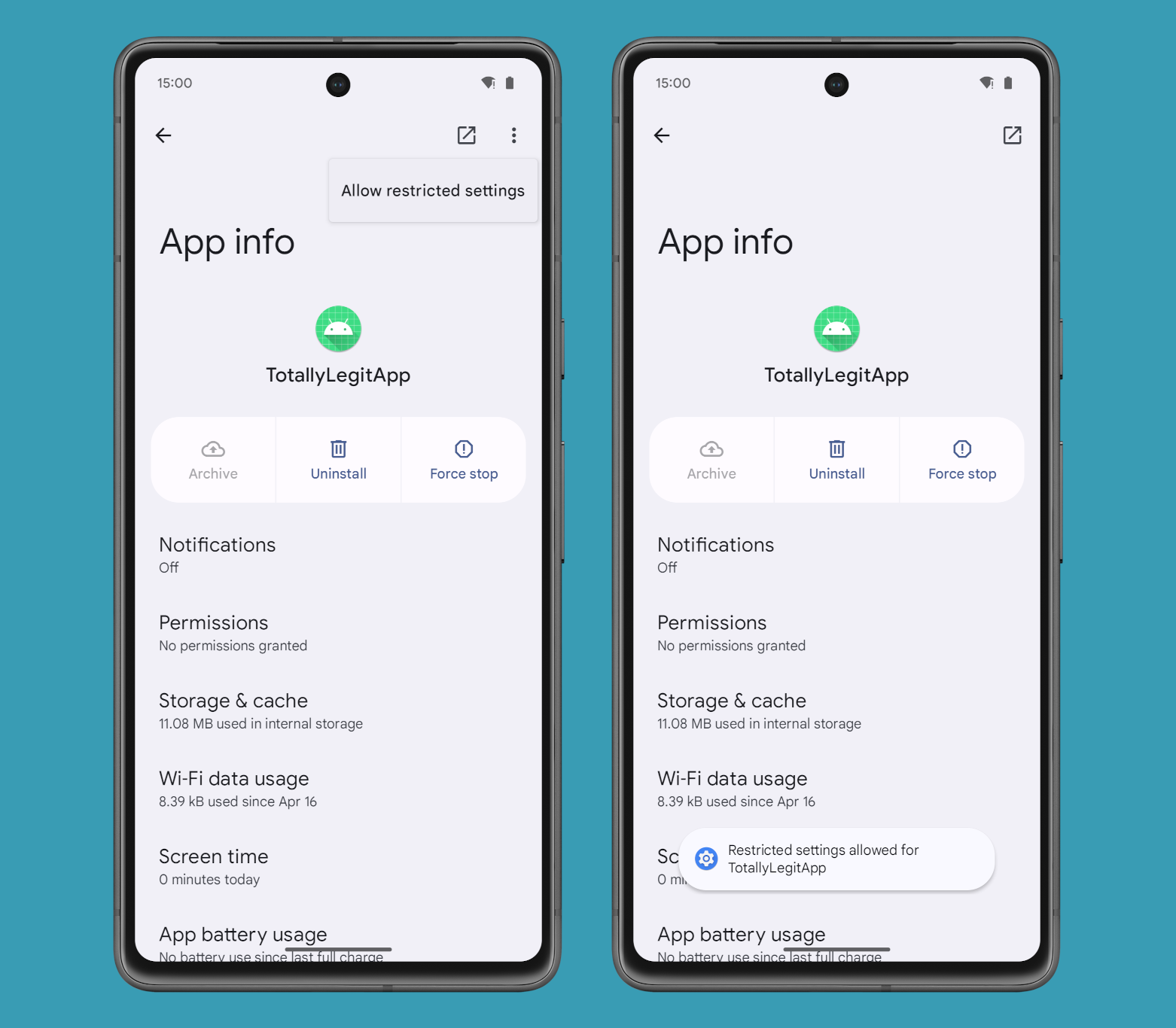
Because of this customers might be compelled to see the Enhanced Affirmation Mode dialog in the event that they attempt to allow an app’s Accessibility or Notification Listener service, supplied the app got here from an untrusted installer or an untrusted supply. This could successfully shut the loophole that existed in Android 13’s Restricted Settings function, making it more durable for malicious third-party apps to realize extremely privileged permissions.
Sadly, I’m undecided whether or not it’ll be potential to nonetheless allow a reliable, sideloaded app’s Accessibility or Notification Listener service if it’s hit with ECM restrictions. It’s potential to disable Restricted Settings for an app, so it also needs to be potential with ECM restrictions, however I can’t say for positive since I haven’t been in a position to get the function to work but in Android 15.
Mishaal Rahman / Android Authority
It’s additionally price noting that presently, zero packages and installers are allowlisted by the system as of Android 15 Beta 1.1. If ECM have been enabled, this could imply that every one apps could be exempt from ECM restrictions, besides these marked as coming from an untrustworthy supply. Since ECM isn’t enabled and there aren’t any allowlisted installers or packages, although, I don’t have any info on how Google plans to make use of this function. Will Google require the Play Retailer to be listed as a trusted installer on all Android units? Which, if any, third-party app shops will Google and OEMs allowlist? These are questions I don’t know the reply to, however regardless, I’m glad to see Google take motion to enhance safety in Android and am trying ahead to discovering out extra particulars about Enhanced Affirmation Mode in Android 15.

